With WEP, you can literally sit in your car listening for packets on a network Once you have captured enough of them, you can extract the key and connect to the network.
WPA-PSK even imposes a eight character minimum on PSK passphrases, making bruteforce attacks less feasible.
security
security, security guard, security cameras, security finance, security service, security systems, security jobs near me, security jobs, security breach fnaf, security breach, security hub, security testing, securitytrails, security code, security headers, security engineer, security council Reset trial period mac adobe flash
Instead of concatenating the key in the IV (the weakness of WEP), WPA hashes they key using the wireless access point's SSID as a salt. Biologia Cellulare E Molecolare Karp Pdf Free

security camera

security through obscurity
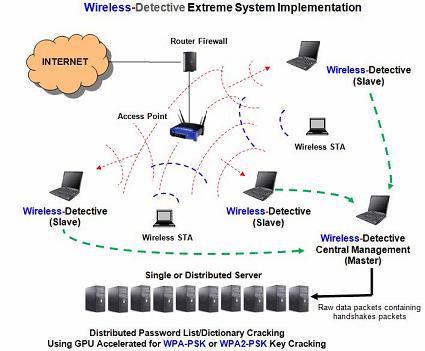
WPA-PSK is particularly susceptible to dictionary attacks against weak passphrases.. It turns out that there's a little back-story there So, in traditional Tarentino fashion, now that we've already seen the ending, let's back up to the beginning: cracking WPA-PSK.. How To Crack WPA / WPA2WEP is much easier to crack than WPA-PSK, as it only requires data capturing (between 20k and 40k packets), while WPA-PSK needs a dictionary attack on a captured.. WPA solves this problem by rotating the key on a per-packet basis, which renders the above method useless.. Perhaps the most predominant flaw in WEP is that the key is not hashed, but concatenated to the IV, allowing completely passive compromise of the network.. We've also added tips for creati Risk Assessment / Security & Hacktivism Battered, but not broken: understanding the WPA crack WiFi security takes a hit with the disclosure of an effective.. So, like virtually all security modalities, the weakness comes down to the passphrase.. It also makes hash precomputation via a technique similar to Rainbow Tables more difficult because the SSID is used as a salt for the hash. 518b7cbc7d


0